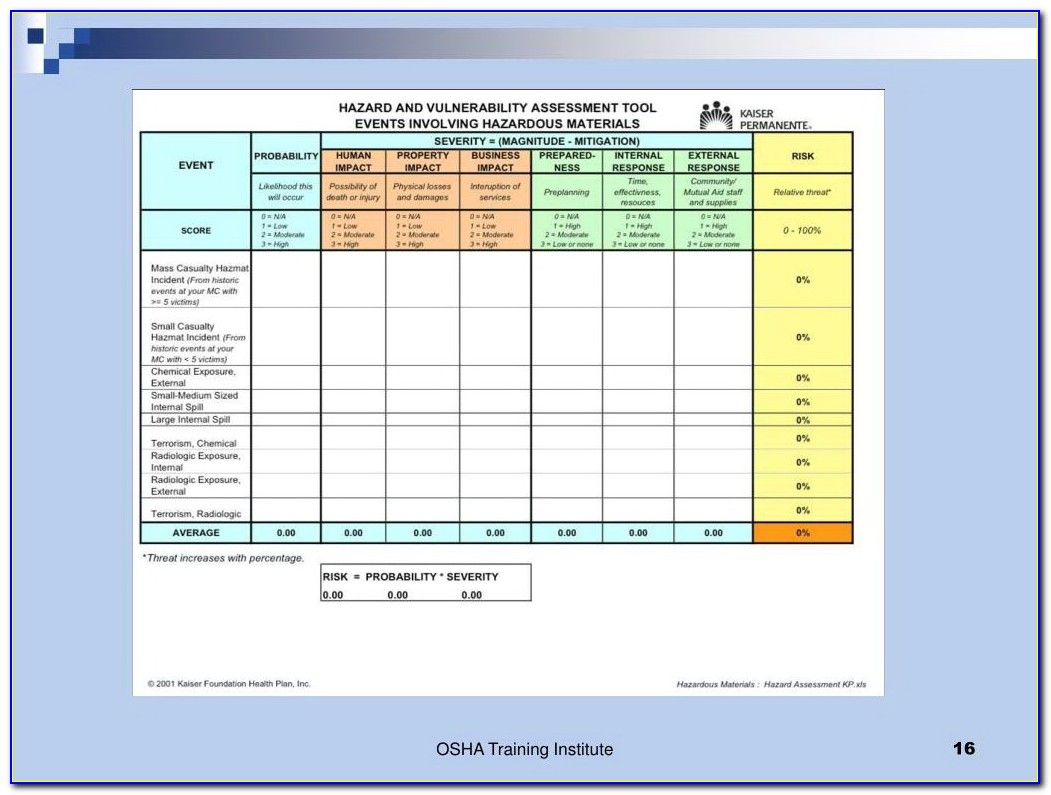
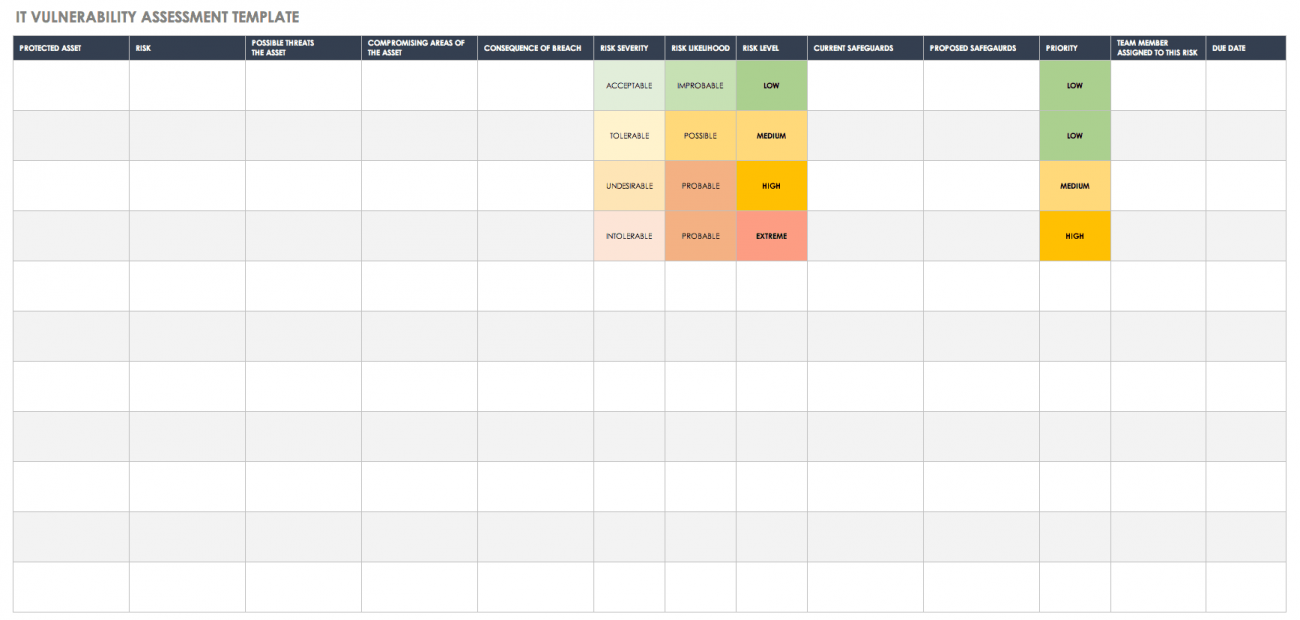
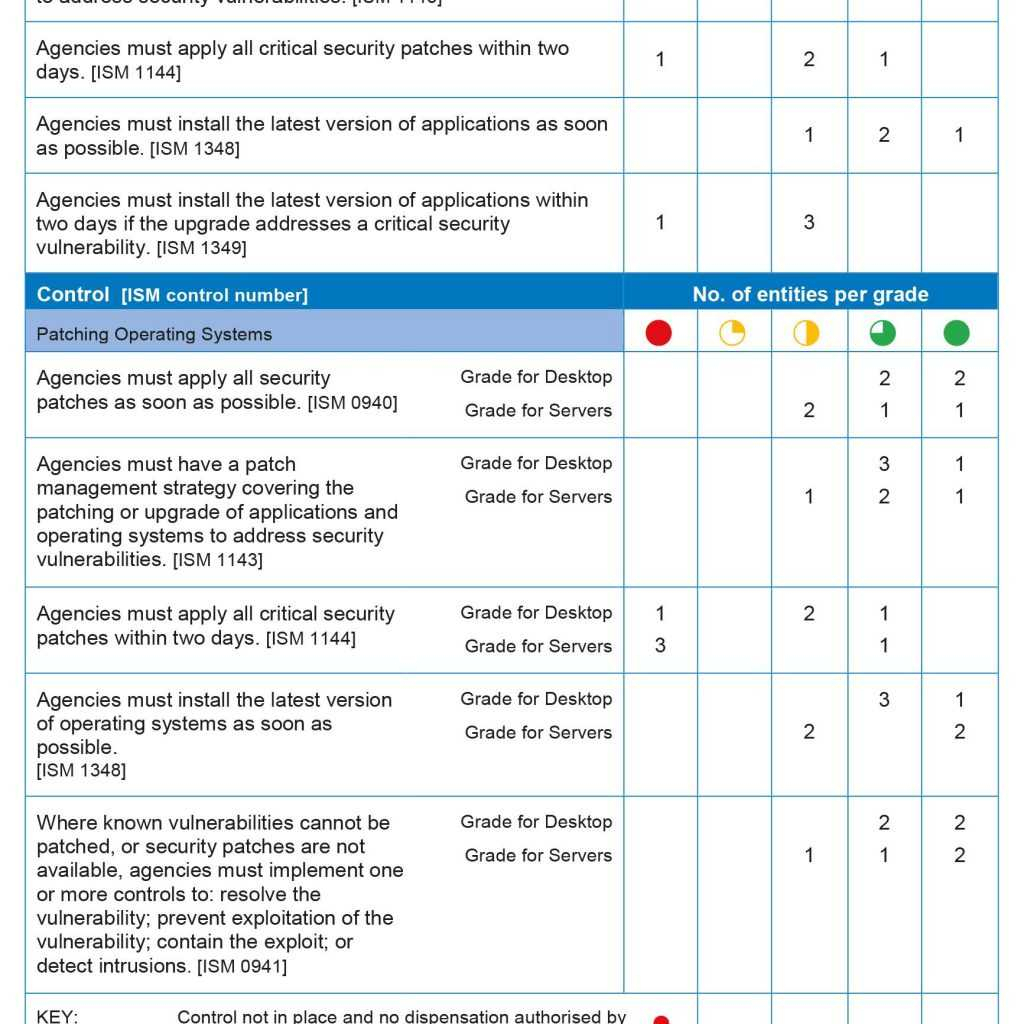
Vulnerability Tracking Spreadsheet Template
Vulnerability Tracking Spreadsheet Template - No matter how carefully planned or implemented, each security measure has its own vulnerable spots. (remember that each pca is listed 4 times). Both spreadsheets have been preformatted for improved data visualization and allow for alternative views of the catalog. Web tracking the results of scanning over time so that you can run reports on the types of vulnerabilities you’re identifying, which vulnerabilities have been addressed and how long they take to fix. The discovery capability requires the expertise to assess the assets and associated processes of the critical services. Web the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess, and prioritize privacy risks to determine how to respond and select appropriate solutions. 87% of customers say quickbooks® simplifies their business finances. Web free vulnerability powerpoint templates. Web to help solve this problem, we put together a list of techniques and tools you can use for vulnerability management tracking. Tips and resources to help improve any vulnerability management. The discovery of vulnerabilities and the analysis of pertinent vulnerabilities. Track, prioritise, and remediate vulnerabilities for robust information security. Provides penalties for failure to comply with this policy No matter how carefully planned or implemented, each security measure has its own vulnerable spots. 7 requirements for vulnerability management tracking systems ; Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment process. Get what you need, they way you like it with odoo project's modern interface. Make a copy of the spreadsheet “gw” and give the new sheet a descriptive name. Web in. Both spreadsheets have been preformatted for improved data visualization and allow for alternative views of the catalog. Tips and resources to help improve any vulnerability management. Get what you need, they way you like it with odoo project's modern interface. Ad organize, schedule, plan and analyze your projects easily with odoo's modern interface. Web learn how to use a penetration. Web get free smartsheet templates. Enhance vulnerability management with our iso 27001 tracking. Web tracking the results of scanning over time so that you can run reports on the types of vulnerabilities you’re identifying, which vulnerabilities have been addressed and how long they take to fix. Each template is fully customizable, so you can tailor your assessment to your business. Web to use the vulnerability ranking spreadsheet follow these steps: Both spreadsheets have been preformatted for improved data visualization and allow for alternative views of the catalog. 7 requirements for vulnerability management tracking systems ; By andy marker | april 5, 2019. Web control catalog spreadsheet (new) the entire security and privacy control catalog in spreadsheet format; By andy marker | april 5, 2019. Web vulnerability remediation tracking is one of the important components of cyber security practices. Enhance vulnerability management with our iso 27001 tracking. Ad manage all your business expenses in one place with quickbooks®. To unlock the full content, please fill out our simple form and receive instant access. 7 requirements for vulnerability management tracking systems ; Both spreadsheets have been preformatted for improved data visualization and allow for alternative views of the catalog. Enhance vulnerability management with our iso 27001 tracking. The purpose of the controlcase vulnerability management policy and procedures templates are to. Web to use the vulnerability ranking spreadsheet follow these steps: Free company profile presentation template with slide layouts like about us, meet the team slide, quote slide and what we do slide. Both spreadsheets have been preformatted for improved data visualization and allow for alternative views of the catalog. 7 requirements for vulnerability management tracking systems ; To unlock the full content, please fill out our simple form and receive. Web download free, customizable vulnerability ranking templates, available in excel, talk, pdf, and google sheets formats. No matter how carefully planned or implemented, each security measure has its own vulnerable spots. 87% of customers say quickbooks® simplifies their business finances. Free company profile presentation template with slide layouts like about us, meet the team slide, quote slide and what we. Free company profile presentation template with slide layouts like about us, meet the team slide, quote slide and what we do slide. Get what you need, they way you like it with odoo project's modern interface. Web the pram is a tool that applies the risk model from nistir 8062 and helps organizations analyze, assess, and prioritize privacy risks to. Web every vulnerability should follow this template. The discovery capability requires the expertise to assess the assets and associated processes of the critical services. Free vulnerability assessment report sample Web any articles, templates, or information provided by smartsheet on the website are for reference only. (remember that each pca is listed 4 times). While we strive to keep the information up to date and correct, we. A vulnerability is a weakness in an application (frequently a broken or missing control) that enables an attack to succeed. Each template is fully customizable, so you can tailor your assessment to your business needs. Web learn how to use a penetration testing report template to document and track the remediation of the vulnerabilities you identify in your systems, networks, or applications. By andy marker | april 5, 2019. Provides penalties for failure to comply with this policy Web free vulnerability powerpoint templates. On the new sheet, delete rows for any pcas that do not exist in any of the zones. Track, prioritise, and remediate vulnerabilities for robust information security. Web it is good practice to identify the type of vulnerability you are dealing with to find adequate and appropriate measures in addressing said vulnerability during the assessment process. Make a copy of the spreadsheet “gw” and give the new sheet a descriptive name. No matter how carefully planned or implemented, each security measure has its own vulnerable spots. Be sure you don’t put [attacks] or [controls] in this category. 87% of customers say quickbooks® simplifies their business finances. Tips and resources to help improve any vulnerability management. Track, prioritise, and remediate vulnerabilities for robust information security. 7 requirements for vulnerability management tracking systems ; Both spreadsheets have been preformatted for improved data visualization and allow for alternative views of the catalog. Web get free smartsheet templates. Ad organize, schedule, plan and analyze your projects easily with odoo's modern interface. Web tracking the results of scanning over time so that you can run reports on the types of vulnerabilities you’re identifying, which vulnerabilities have been addressed and how long they take to fix. Web to use the vulnerability ranking spreadsheet follow these steps: Web control catalog spreadsheet (new) the entire security and privacy control catalog in spreadsheet format; Web learn how to use a penetration testing report template to document and track the remediation of the vulnerabilities you identify in your systems, networks, or applications. Be sure you don’t put [attacks] or [controls] in this category. Tenable vulnerability management provides a selection of report templates and customizable. For more information, see the fedramp product offering. Web download free, customizable vulnerability ranking templates, available in excel, talk, pdf, and google sheets formats. While we strive to keep the information up to date and correct, we. Web to help solve this problem, we put together a list of techniques and tools you can use for vulnerability management tracking. This tool will allow you to track vulnerabilities from the point when they were identified to when they are remediated.Vulnerability Tracking Spreadsheet for Vulnerability Management Metrics
Vulnerability Tracking Spreadsheet in Outstanding Remediations Tracking
Vulnerability Tracking Spreadsheet inside Vulnerability Tracking
Vulnerability Tracking Spreadsheet pertaining to Excel Spreadsheet
Vulnerability Tracking Spreadsheet Spreadsheet Downloa vulnerability
Web Vulnerability Assessment Report Template Template Resume
Free Vulnerability Assessment Templates Smartsheet
Vulnerability Tracking Spreadsheet Spreadsheet Downloa vulnerability
Patch Management Spreadsheet within Network Vulnerability Assessment
Vulnerability Tracking Spreadsheet for Debt Management Spreadsheet And
Web Creating And Implementing An Vulnerability Management Policies And Procedures Is A Vital Component Of Any Company’s Cyber Security Strategy, And Is Required By Several Standards Including:
Most Vulnerability Data Comes From Scanners, Though The Most Important Vulnerability Data Often Comes From Humans.
To Unlock The Full Content, Please Fill Out Our Simple Form And Receive Instant Access.
87% Of Customers Say Quickbooks® Simplifies Their Business Finances.
Related Post: