Phishing Email Response Template
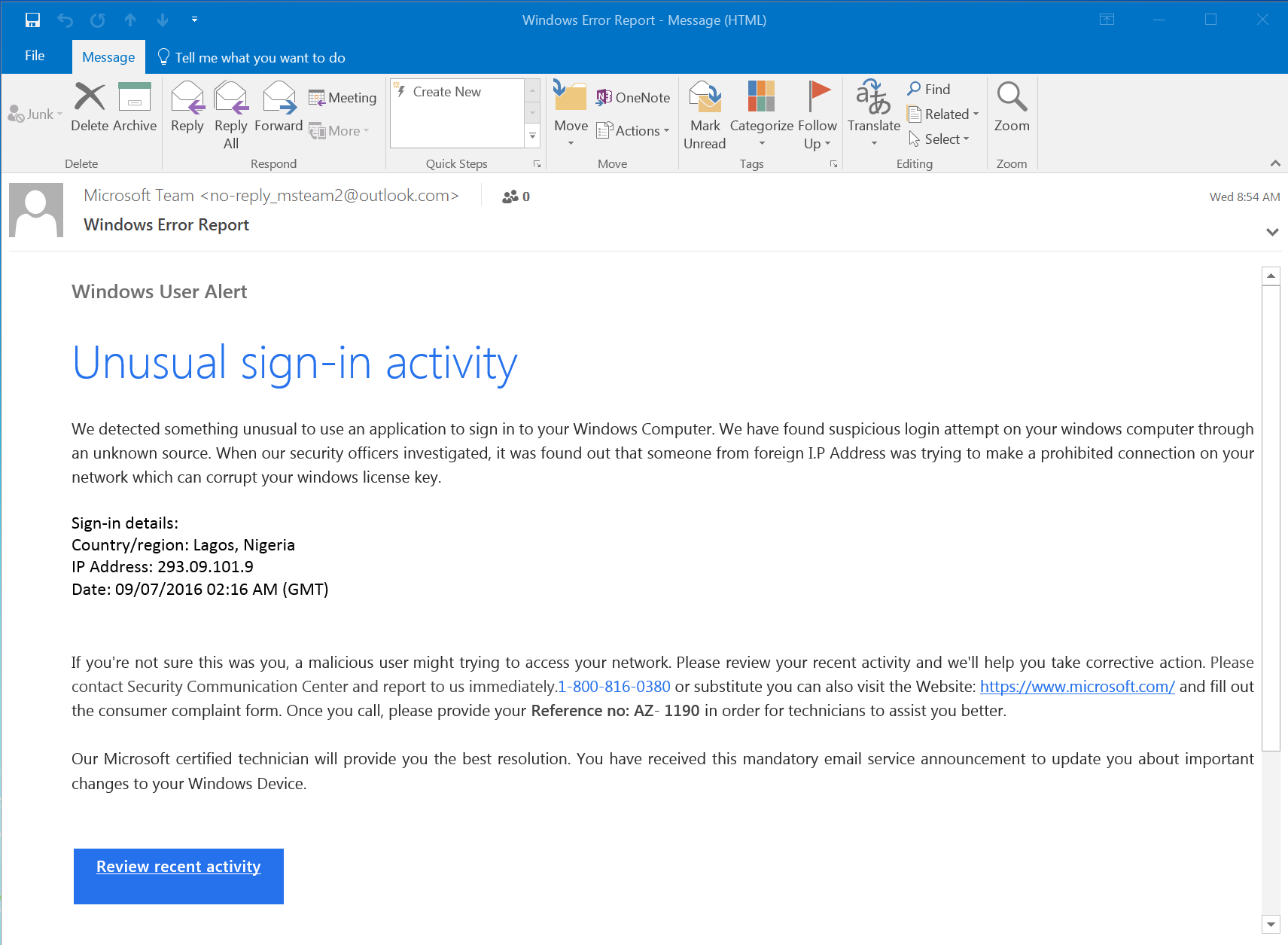
Phishing Email Response Template - Suspicious activity on your account. Web combat email and cloud threats. Attacks can come from scammers disguised as trustworthy sources to get sensitive data. Web internet security cto at aura identity theft and fraud protection for your finances, personal info, and devices. In the alerts tab of the incident, alerts from defender for office 365 and microsoft defender for cloud. How well do you know your inbox? Report an email as phishing. How to label a phishing simulation template?. Every organization — and every employee — is susceptible to different types of phishing emails. Web the odds are that the email is an example of phishing, an attempt by scammers to trick you into providing personal or financial information that they can then. In the alerts tab of the incident, alerts from defender for office 365 and microsoft defender for cloud. Use them with great responsibility. Web cybercriminals have been successful using emails, text messages, and direct messages on social media or in video games, to get people to respond with their personal information. Ad while phishing scams and cyberthreats are constantly evolving,. It's also the most common way for organizations to be. Get these emails as a free pdf ups failed delivery attempt this email is incredibly. This makes simulating a wide variety. Report an email as phishing. How to label a phishing simulation template?. Knowbe4's phish alert button gives your users a safe way to forward email threats to the security team for. Suspicious activity on your account. What does your response email look like? Web cybercriminals have been successful using emails, text messages, and direct messages on social media or in video games, to get people to respond with their personal information. Ad. Get these emails as a free pdf ups failed delivery attempt this email is incredibly. In fact, the fbi estimatesthat more than $1.75 billion was lost to business email scams like phishing in 2019. Ad while phishing scams and cyberthreats are constantly evolving, you can protect yourself. It's also the most common way for organizations to be. Web google may. Get these emails as a free pdf ups failed delivery attempt this email is incredibly. Report an email as phishing. Web combat email and cloud threats. Web for endpoint compromise, an attacker will craft a phishing email that contains a malicious attachment, enticing the victim into downloading and opening it. Every organization — and every employee — is susceptible to. Attacks can come from scammers disguised as trustworthy sources to get sensitive data. What does your response email look like? Web the odds are that the email is an example of phishing, an attempt by scammers to trick you into providing personal or financial information that they can then. Web cybercriminals have been successful using emails, text messages, and direct. How to label a phishing simulation template?. Ad while phishing scams and cyberthreats are constantly evolving, you can protect yourself. How well do you know your inbox? Web cybercriminals have been successful using emails, text messages, and direct messages on social media or in video games, to get people to respond with their personal information. Web for endpoint compromise, an. Web pharming phishing attacks work by tricking people into giving up their sensitive information, but pharming tricks computers by changing domain name system (dns) settings on a. Every organization — and every employee — is susceptible to different types of phishing emails. Web the odds are that the email is an example of phishing, an attempt by scammers to trick. Attacks can come from scammers disguised as trustworthy sources to get sensitive data. Get these emails as a free pdf ups failed delivery attempt this email is incredibly. Web internet security cto at aura identity theft and fraud protection for your finances, personal info, and devices. Tue, 18 jan, 2022 at 4:22 pm table of contents how to customize a. How to label a phishing simulation template?. Suspicious activity on your account. What key points do you make in. Get these emails as a free pdf ups failed delivery attempt this email is incredibly. Ad while phishing scams and cyberthreats are constantly evolving, you can protect yourself. In the alerts tab of the incident, alerts from defender for office 365 and microsoft defender for cloud. Every organization — and every employee — is susceptible to different types of phishing emails. Do not open any suspicious email based on. What key points do you make in. This makes simulating a wide variety. On a computer, go to gmail. It's also the most common way for organizations to be. Web pharming phishing attacks work by tricking people into giving up their sensitive information, but pharming tricks computers by changing domain name system (dns) settings on a. Web template for responding to phishing email inquiries a user wants confirmation if a link is safe to visit. Use them with great responsibility. How to label a phishing simulation template?. Suspicious activity on your account. Web do your users know what to do when they receive a phishing email? How well do you know your inbox? Protect your people from email and cloud threats with an intelligent and holistic approach. Web for endpoint compromise, an attacker will craft a phishing email that contains a malicious attachment, enticing the victim into downloading and opening it. Knowbe4's phish alert button gives your users a safe way to forward email threats to the security team for. Web here are our top 10 phishing email templates. In fact, the fbi estimatesthat more than $1.75 billion was lost to business email scams like phishing in 2019. Web the odds are that the email is an example of phishing, an attempt by scammers to trick you into providing personal or financial information that they can then. Attacks can come from scammers disguised as trustworthy sources to get sensitive data. Web internet security cto at aura identity theft and fraud protection for your finances, personal info, and devices. Tue, 18 jan, 2022 at 4:22 pm table of contents how to customize a phishing email template? What key points do you make in. Web the odds are that the email is an example of phishing, an attempt by scammers to trick you into providing personal or financial information that they can then. Web do your users know what to do when they receive a phishing email? Web combat email and cloud threats. Suspicious activity on your account. Get these emails as a free pdf ups failed delivery attempt this email is incredibly. In fact, the fbi estimatesthat more than $1.75 billion was lost to business email scams like phishing in 2019. How to label a phishing simulation template?. Web pharming phishing attacks work by tricking people into giving up their sensitive information, but pharming tricks computers by changing domain name system (dns) settings on a. Web here are our top 10 phishing email templates. How well do you know your inbox? Web google may analyze these emails and attachments to help protect our users from spam and abuse. In the alerts tab of the incident, alerts from defender for office 365 and microsoft defender for cloud.Stories & Examples Phishing Education & Training Indiana University
Create a Phishing Simulation Campaign TrendMicro
Test your employees with a simulated phishing attack NetSol IT
Examples of Phishing Emails IT Assurance and Cyber Security
19 Examples of Common Phishing Emails Terranova Security
Phishing Email Alert Design Template Stock Vector Illustration of
ReplyTo Phishing Knowledge Base
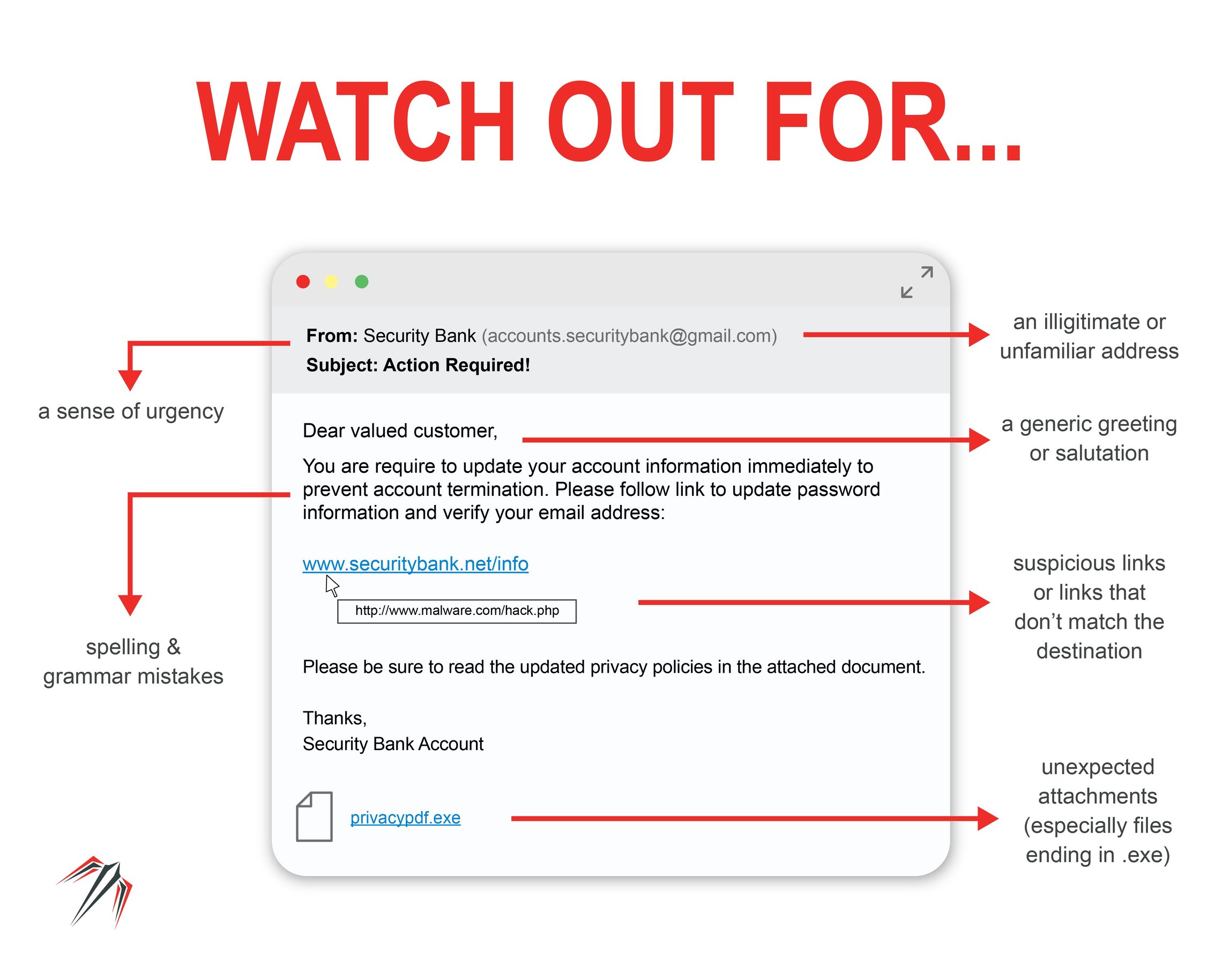
Don’t Get Hooked! 7 Signs of a Phishing Email
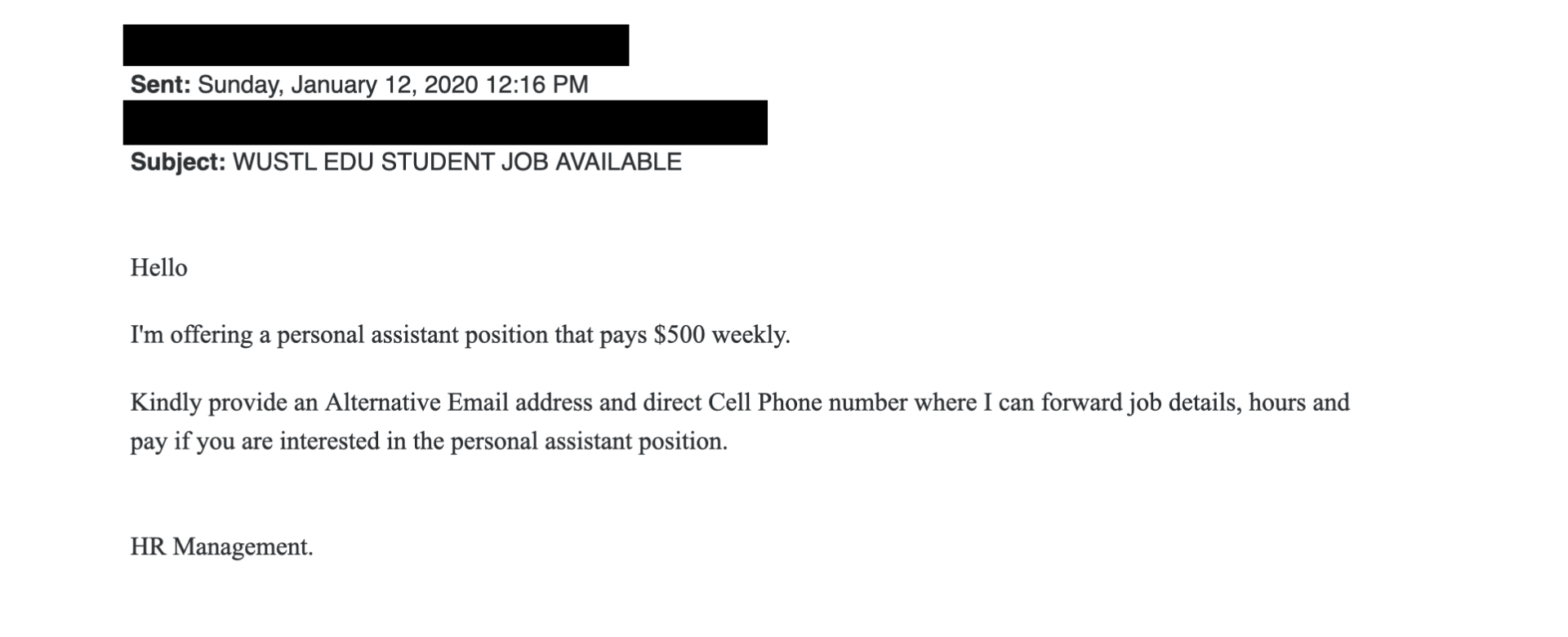
Phishing Alert Fraudulent Student Job Offer Office of Information
What Is Phishing And How To Prevent It From Happening
What Does Your Response Email Look Like?
Web Template For Responding To Phishing Email Inquiries A User Wants Confirmation If A Link Is Safe To Visit.
Report An Email As Phishing.
Do Not Open Any Suspicious Email Based On.
Related Post: