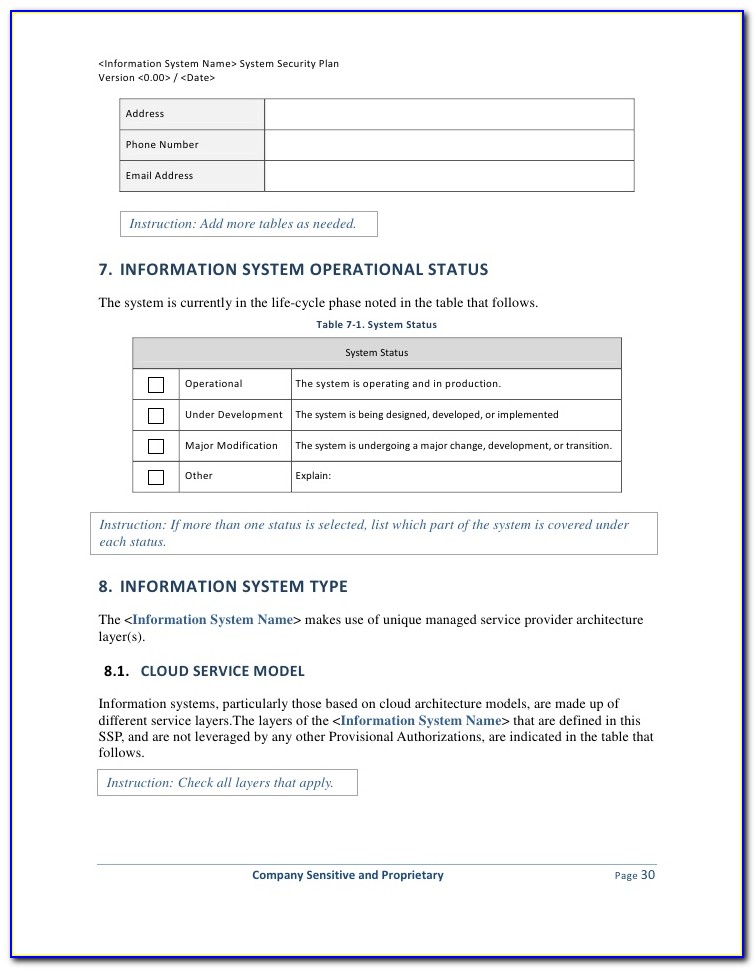
Nist Information Security Policy Template
Nist Information Security Policy Template - Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program. Supply chain risk management (id.sc) 3 nist function: These are free to use and fully customizable to your company's it security practices. The nist 800 template download contains a.doc file template and xls templates for poams, federal, state, cloud based and a legacy template as well as. To do nist csf, iso 27002 or. To the five main pillars of a successful cybersecurity program, nist now has added a sixth,. Web the purpose of this document is to assist federal agencies in protecting the confidentiality of personally identifiable information (pii) in information systems. Web this nist cybersecurity practice guide explains how commercially available technology can be integrated and used to build various ztas. Web nist drafts major update to its widely used cybersecurity framework. Abbreviations / acronyms / synonyms: These are free to use and fully customizable to your company's it security practices. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program. Web security models are formal presentations of the security policy enforced by the system, and are useful for proving theoretical limitations of a system.. Nist information system contingency plan templates for high, moderate, and low systems. Asset management (id.am) 2 identify: Web planning guides linkedin email this section includes resources to help you create, evaluate, and improve your business’ overall security plan. Rocketlawyer.com has been visited by 100k+ users in the past month Resources include, but are not limited to: Rocketlawyer.com has been visited by 100k+ users in the past month Web this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and. Approaches, methodologies, implementation guides, mappings to the framework, case. The framework has been used widely to reduce cybersecurity risks. Web this nist cybersecurity practice guide explains how. These are free to use and fully customizable to your company's it security practices. The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal. Web this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and. The framework has been used. Web this nist cybersecurity practice guide explains how commercially available technology can be integrated and used to build various ztas. To do nist csf, iso 27002 or. Web to accomplish technical security assessments and ensure that technical security testing and examinations provide maximum value, nist recommends that organizations:. The framework has been used widely to reduce cybersecurity risks. Supply chain. Web nist drafts major update to its widely used cybersecurity framework. Web to accomplish technical security assessments and ensure that technical security testing and examinations provide maximum value, nist recommends that organizations:. This special publication 800 series reports. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program.. Nvd score not yet provided. The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal. This special publication 800 series reports. Web sans has developed a set of information security policy templates. The nist 800 template download contains a.doc file template and xls templates for poams, federal, state, cloud based and. This special publication 800 series reports. Web nist drafts major update to its widely used cybersecurity framework. The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal. Web this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and. Nvd score. To do nist csf, iso 27002 or. Web planning guides linkedin email this section includes resources to help you create, evaluate, and improve your business’ overall security plan. Rocketlawyer.com has been visited by 100k+ users in the past month The nist 800 template download contains a.doc file template and xls templates for poams, federal, state, cloud based and a legacy. These are free to use and fully customizable to your company's it security practices. Abbreviations / acronyms / synonyms: Web this nist cybersecurity practice guide explains how commercially available technology can be integrated and used to build various ztas. Web sans has developed a set of information security policy templates. To do nist csf, iso 27002 or. The framework has been used widely to reduce cybersecurity risks. These are free to use and fully customizable to your company's it security practices. To the five main pillars of a successful cybersecurity program, nist now has added a sixth,. Web planning guides linkedin email this section includes resources to help you create, evaluate, and improve your business’ overall security plan. Web nist drafts major update to its widely used cybersecurity framework. Resources include, but are not limited to: Web to accomplish technical security assessments and ensure that technical security testing and examinations provide maximum value, nist recommends that organizations:. Web this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and. Web this is the public draft of the nist cybersecurity framework (csf or framework) 2.0. Asset management (id.am) 2 identify: Web this nist cybersecurity practice guide explains how commercially available technology can be integrated and used to build various ztas. The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal. Web nist is responsible for developing standards and guidelines, including minimum requirements, for providing adequate information security for all agency operations and. Supply chain risk management (id.sc) 3 nist function: Web the purpose of this document is to assist federal agencies in protecting the confidentiality of personally identifiable information (pii) in information systems. Approaches, methodologies, implementation guides, mappings to the framework, case. To do nist csf, iso 27002 or. This special publication 800 series reports. Web nist cybersecurity framework v1.0 (page not in english) (this is a direct translation of version 1.0 of the cybersecurity framework produced by the government. Aggregate of directives, regulations, rules, and practices that prescribes how an organization manages, protects, and distributes. Web to accomplish technical security assessments and ensure that technical security testing and examinations provide maximum value, nist recommends that organizations:. Resources include, but are not limited to: Nvd score not yet provided. Supply chain risk management (id.sc) 3 nist function: Web nist drafts major update to its widely used cybersecurity framework. Web planning guides linkedin email this section includes resources to help you create, evaluate, and improve your business’ overall security plan. These are free to use and fully customizable to your company's it security practices. This special publication 800 series reports. Web nist cybersecurity framework v1.0 (page not in english) (this is a direct translation of version 1.0 of the cybersecurity framework produced by the government. Web security models are formal presentations of the security policy enforced by the system, and are useful for proving theoretical limitations of a system. Web sans has developed a set of information security policy templates. Abbreviations / acronyms / synonyms: Web this nist cybersecurity practice guide explains how commercially available technology can be integrated and used to build various ztas. Web this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program. Nist information system contingency plan templates for high, moderate, and low systems.Data Classification Policy Template Nist
Information Security Policy Template Nist Template 1 Resume
It Security Policy Template Nist Template 1 Resume Examples 7NYAXnb9pv
Nist Information Security Policy Template
Nist Information Security Policy Template merrychristmaswishes.info
Nist Personnel Security Policy Template Template Resume Examples
Nist Information Security Policy Template Master of
Nist Information Security Policy Template Master of
Nist Information Security Policy Template merrychristmaswishes.info
Nist Information Security Policy Template merrychristmaswishes.info
Web Nist Is Responsible For Developing Standards And Guidelines, Including Minimum Requirements, For Providing Adequate Information Security For All Agency Operations And.
Aggregate Of Directives, Regulations, Rules, And Practices That Prescribes How An Organization Manages, Protects, And Distributes.
Web The Purpose Of This Document Is To Assist Federal Agencies In Protecting The Confidentiality Of Personally Identifiable Information (Pii) In Information Systems.
Asset Management (Id.am) 2 Identify:
Related Post: