Key Control Policy Template
Key Control Policy Template - This guide gives the correlation between 49 of. Web this document defines the policies that govern key and electronic access control at keene state college. For use of this form see ar 190. Web key request form on behalf of the employee with the lost or stolen key. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web an internal control is an action your department takes to prevent and detect errors, omissions, or potential fraudulent transactions in its financial statements. Requestor may only request keys for areas assigned under their control. Web a comprehensive key control policy protects your organization’s most valuable your. Also see this plan loaded into monday.com, an online collaboration tool that. Web policy it is the policy of facilities management to limit and tightly control the number of keys to university facilities and spaces. A replacement for a worn or broken key will be provided by exchange for the defective. The kca comprises the person,persons,department,or committee that has authority to adopt,administer,and enforce this facility’s key management policy. Web key request form on behalf of the employee with the lost or stolen key. Web our policy template, enterprise asset management policy, is meant to supplement. Key shop if keys are missing, the individual will make. You can create and manage key policies in the aws kms console, by using aws kms api operations, such as createkey, replicatekey, and putkeypolicy, or by. Policy keene state college shall maintain a locking. A replacement for a worn or broken key will be provided by exchange for the defective.. The department head that administers the particular area must also approve all key. This guide gives the correlation between 49 of. To set forth the procedures for institutional control of keys and to provide procedures for requesting. For use of this form see ar 190. The policy statements included within this document can be used by all cis. This guide gives the correlation between 49 of. Web residence life office housing office will notify physical plant of lost keys and charge students appropriately. A security department has the sole and exclusive responsibility and authority for all locks and keys (physical, electronic or of any other. You can create and manage key policies in the aws kms console, by. Web this document defines the policies that govern key and electronic access control at keene state college. Web our policy template, enterprise asset management policy, is meant to supplement the cis controls v8. A replacement for a worn or broken key will be provided by exchange for the defective. Web an internal control is an action your department takes to. The department head that administers the particular area must also approve all key. Web mcneese state university has developed this key control policy to achieve accountability for all keys to university buildings and/or offices, to provide. Web an internal control is an action your department takes to prevent and detect errors, omissions, or potential fraudulent transactions in its financial statements.. Requestor may only request keys for areas assigned under their control. Web key request form on behalf of the employee with the lost or stolen key. Web sample key control procedure. A security department has the sole and exclusive responsibility and authority for all locks and keys (physical, electronic or of any other. Key shop if keys are missing, the. Web our policy template, enterprise asset management policy, is meant to supplement the cis controls v8. Web an internal control is an action your department takes to prevent and detect errors, omissions, or potential fraudulent transactions in its financial statements. For use of this form see ar 190. Key shop if keys are missing, the individual will make. The policy. This policy provides guidance and procedures for the control of keys to promote the safety and security of the college. Web policy it is the policy of facilities management to limit and tightly control the number of keys to university facilities and spaces. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf).. To set forth the procedures for institutional control of keys and to provide procedures for requesting. For the purposes of this policy, this would. Web mcneese state university has developed this key control policy to achieve accountability for all keys to university buildings and/or offices, to provide. Web an internal control is an action your department takes to prevent and. Proper care and handling of keys and locks all staff shall be trained in and held responsible for adhering to proper procedures for the. Requestor may only request keys for areas assigned under their control. Web download this excel control plan template and update the header information to suit your business. This policy provides guidance and procedures for the control of keys to promote the safety and security of the college. A replacement for a worn or broken key will be provided by exchange for the defective. Policy keene state college shall maintain a locking. For the purposes of this policy, this would. Web a comprehensive key control policy protects your organization’s most valuable your. To set forth the procedures for institutional control of keys and to provide procedures for requesting. Web mcneese state university has developed this key control policy to achieve accountability for all keys to university buildings and/or offices, to provide. Web our policy template, enterprise asset management policy, is meant to supplement the cis controls v8. Also see this plan loaded into monday.com, an online collaboration tool that. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Here are 9 staircase to implement essential control procedures for max. Web this document defines the policies that govern key and electronic access control at keene state college. For use of this form see ar 190. Web residence life office housing office will notify physical plant of lost keys and charge students appropriately. All keys to university facilities and spaces are. The department head that administers the particular area must also approve all key. This guide gives the correlation between 49 of. You can create and manage key policies in the aws kms console, by using aws kms api operations, such as createkey, replicatekey, and putkeypolicy, or by. Requestor may only request keys for areas assigned under their control. To set forth the procedures for institutional control of keys and to provide procedures for requesting. The kca comprises the person,persons,department,or committee that has authority to adopt,administer,and enforce this facility’s key management policy. Proper care and handling of keys and locks all staff shall be trained in and held responsible for adhering to proper procedures for the. Web mcneese state university has developed this key control policy to achieve accountability for all keys to university buildings and/or offices, to provide. Policy keene state college shall maintain a locking. Web an internal control is an action your department takes to prevent and detect errors, omissions, or potential fraudulent transactions in its financial statements. Web residence life office housing office will notify physical plant of lost keys and charge students appropriately. All keys to university facilities and spaces are. Web sample key control procedure. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). The policy statements included within this document can be used by all cis. Web key request form on behalf of the employee with the lost or stolen key. The department head that administers the particular area must also approve all key. Here are 9 staircase to implement essential control procedures for max.Cryptographic Key Management Policy Template
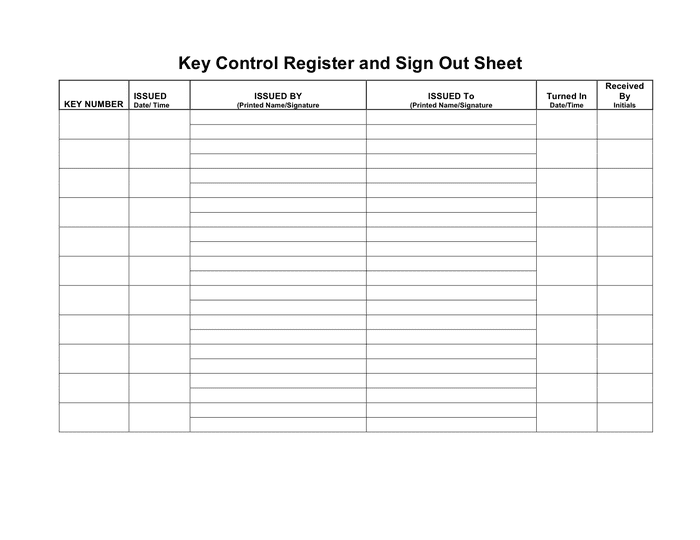
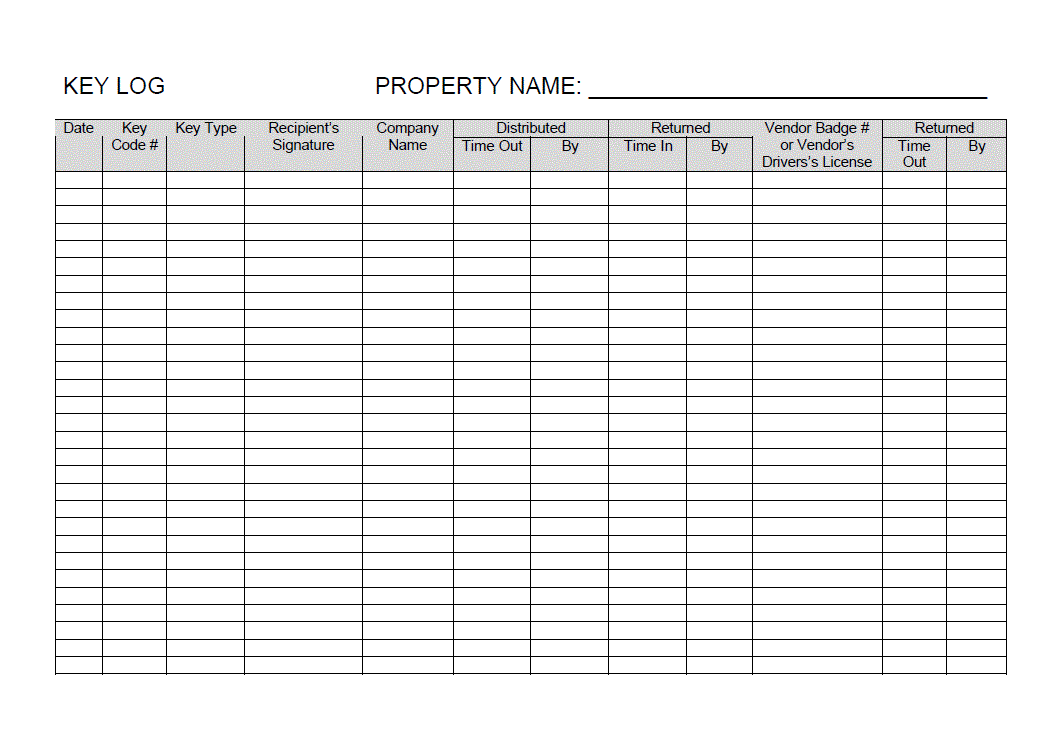
Key control register and sign out sheet in Word and Pdf formats page
Awesome Key Control Policy Template Sparklingstemware in 2021
Encryption Key Management Policy Template Policy template, Enterprise
Key Control Policy Template Theearthe
Key Control
Standard Access Control Policy Template Free Download
Key Control Policy and Procedures Manual 1
Key Control Policy Template Flyer Template
Cryptographic Key Management Policy Template High Table
For The Purposes Of This Policy, This Would.
This Guide Gives The Correlation Between 49 Of.
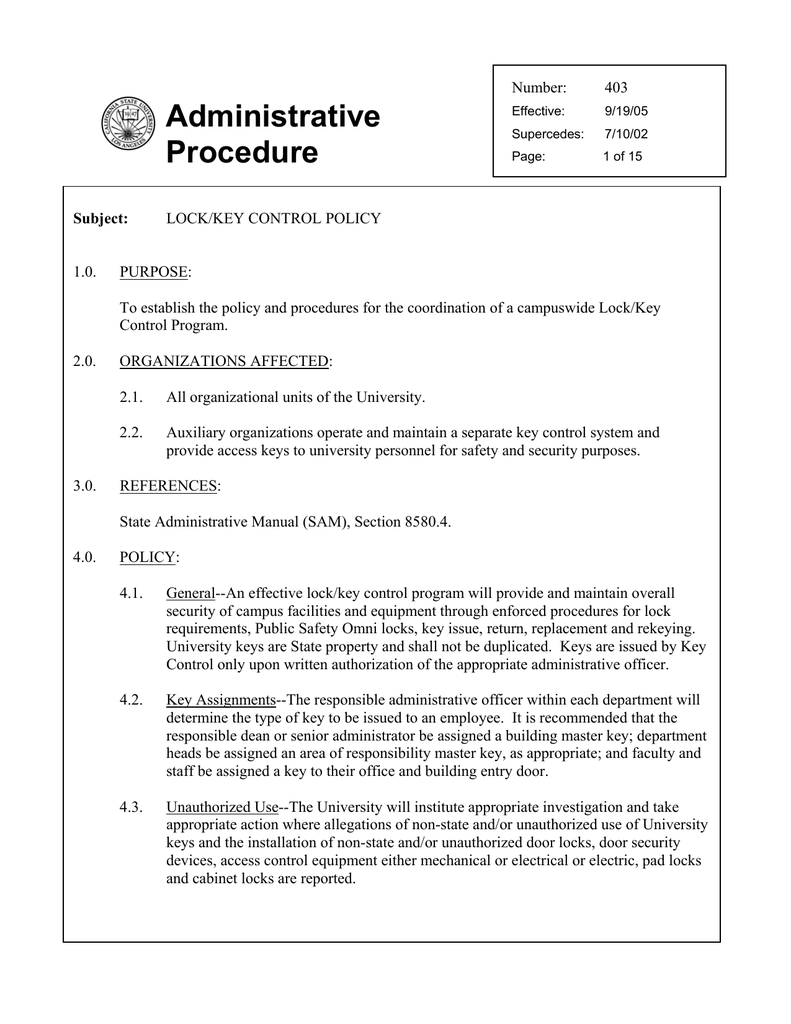
Web Key Control Administrative Policies And Procedures Purpose:
A Replacement For A Worn Or Broken Key Will Be Provided By Exchange For The Defective.
Related Post: