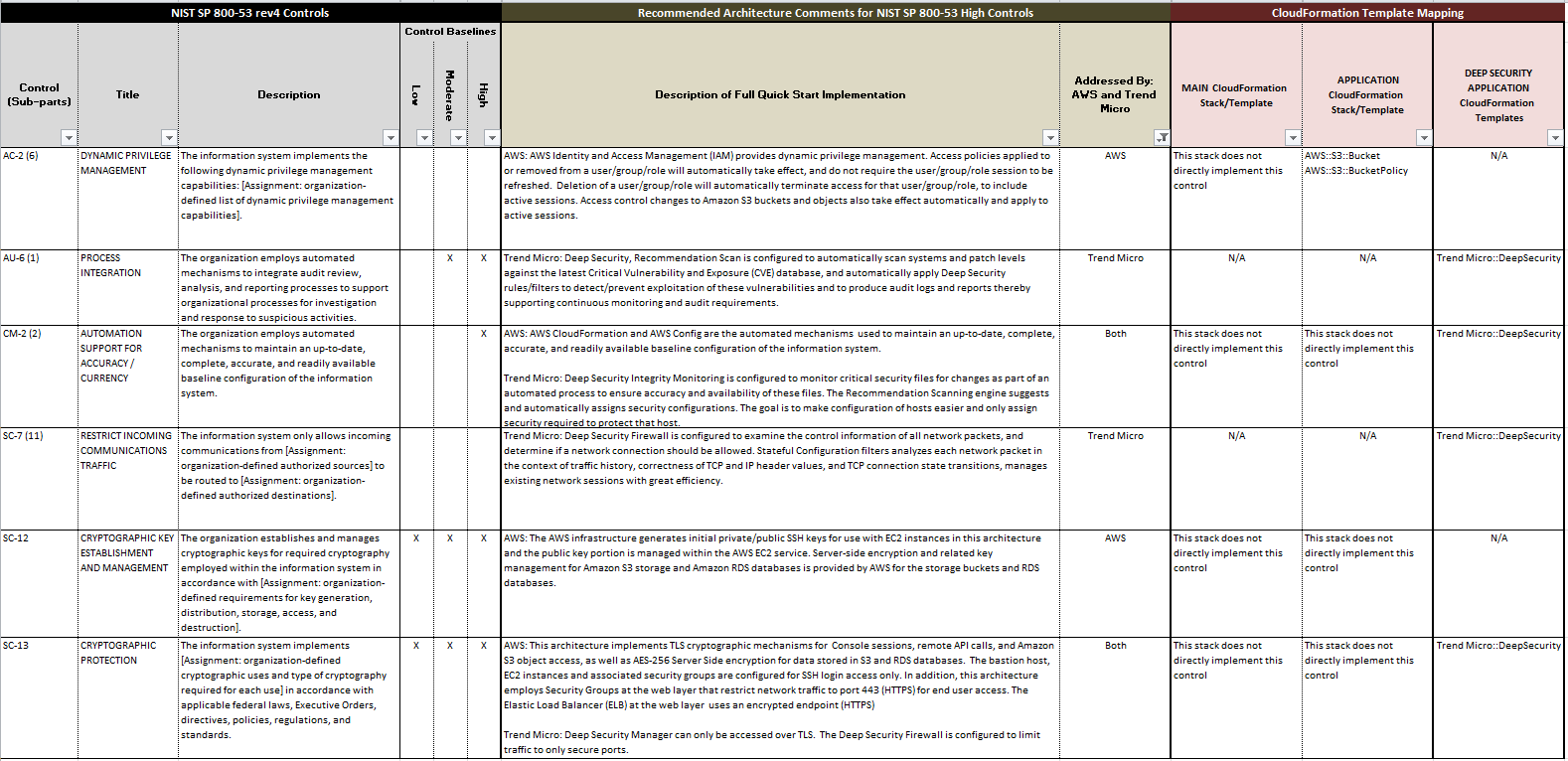
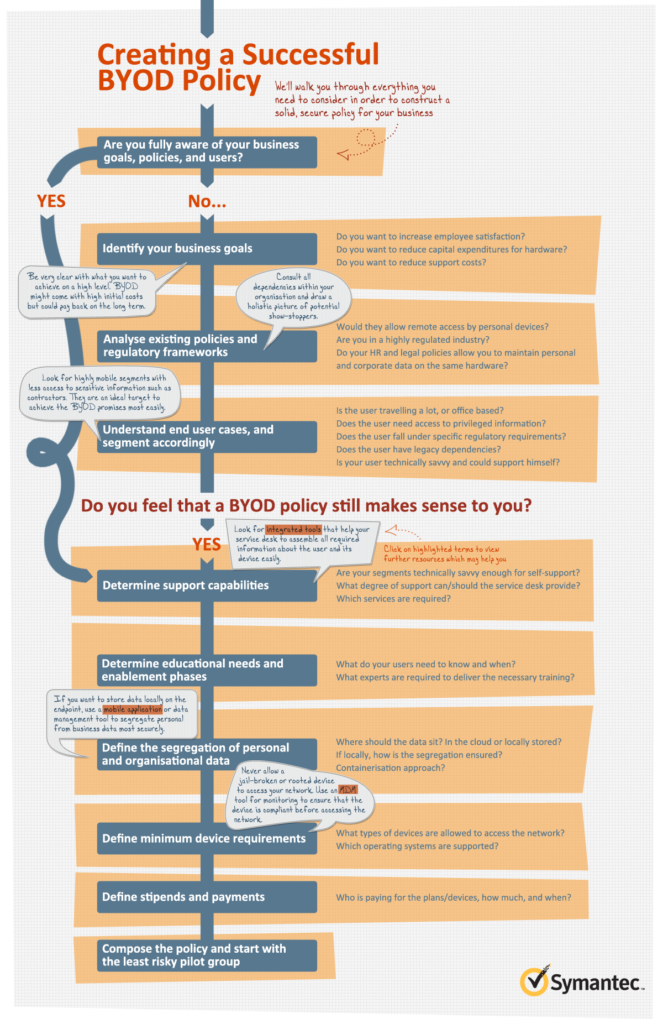
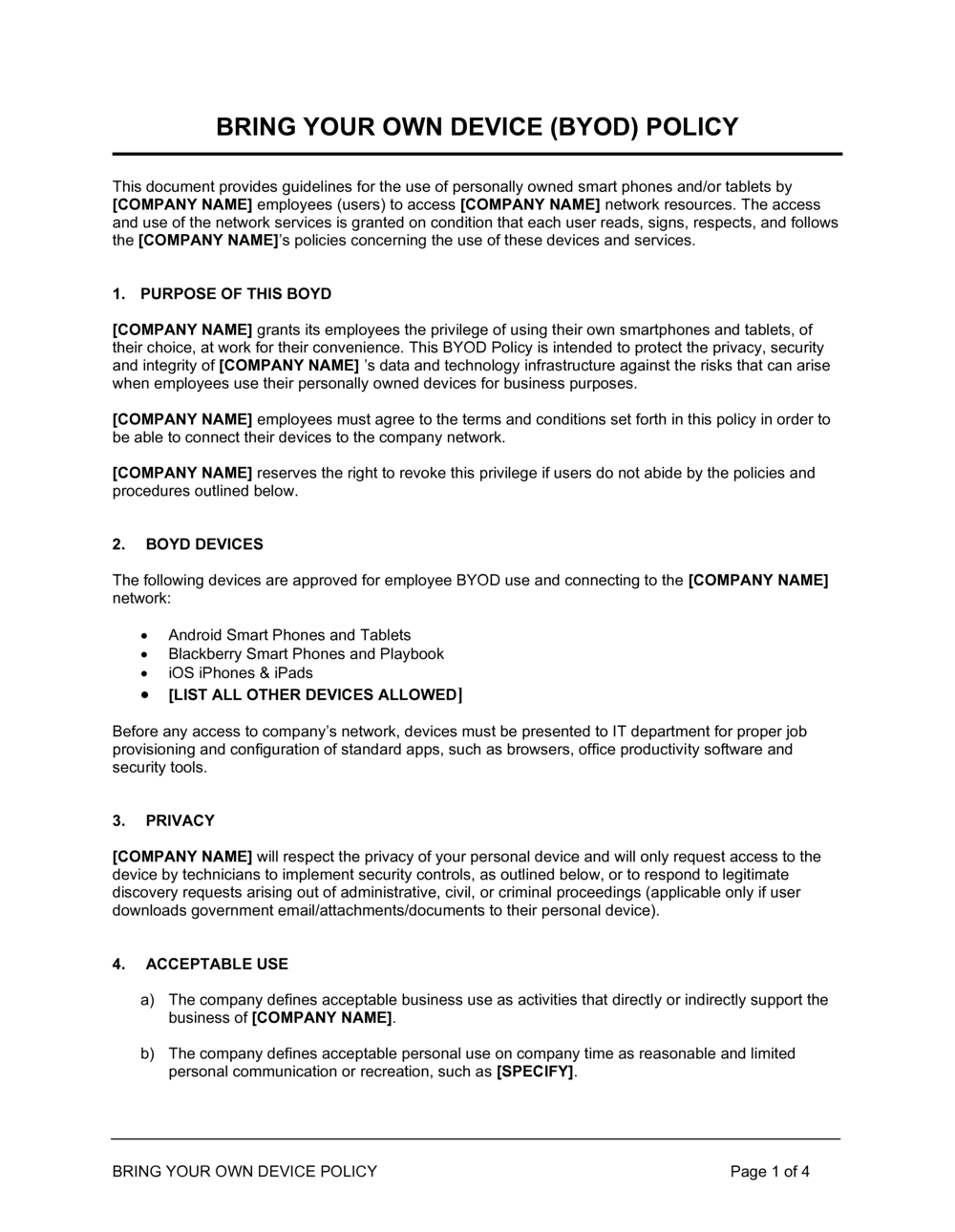
Byod Policy Template Nist
Byod Policy Template Nist - The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal agencies. Web your own device (byod). Web this publication provides information on security considerations for several types of remote access solutions, and it makes recommendations for securing a variety. This practice guide provides an example. Ad haven't done a dfars assessment? Cybersecurity challenges, is aligned with leading practices. This publication provides recommendations for securing byod devices used for telework and remote access, as well as those directly attached to the. Security for enterprise telework, remote access, and bring your own device (byod) solutions; Web itl march 2020 bulletin: Web each telework device is controlled by the organization, a third party (such as the organization's contractors, business partners, and vendors), or the teleworker; Web your own device (byod). Web may 6, 2013 download all papers are copyrighted. It also gives advice on creating related security policies. Web protected when it is accessed from personal devices poses unique challenges and threats. Web each telework device is controlled by the organization, a third party (such as the organization's contractors, business partners, and vendors), or the. Web itl march 2020 bulletin: These are free to use and fully customizable to your company's it security practices. Web this publication provides information on security considerations for several types of remote access solutions, and it makes recommendations for securing a variety. This publication provides recommendations for securing byod devices used for telework and remote access, as well as those. Web nist seeks feedback on whether this draft revision addresses organizations’ current and anticipated future. To improve the security of organizations’ telework and remote access technologies, as well as better. Security for enterprise telework, remote access, and bring your own device (byod) solutions; Cybersecurity challenges, is aligned with leading practices. Web itl march 2020 bulletin: This practice guide provides an example. Finding an effective solution can be challenging due to the 63 unique risks that byod deployments impose. 0 purpose to describe the conditions under which our employees my use their own devices at work. The growing ubiquity of computing devices, whether it is a home computer or a personal smartphone, means that more and. Web this publication provides information on security considerations for several types of remote access solutions, and it makes recommendations for securing a variety. It also gives advice on creating related security policies. Web may 6, 2013 download all papers are copyrighted. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Web byod. 0 purpose to describe the conditions under which our employees my use their own devices at work. Ad haven't done a dfars assessment? After considering more than a year’s. This publication provides recommendations for securing byod devices used for telework and remote access, as well as those directly attached to the. Web sans has developed a set of information security. To improve the security of organizations’ telework and remote access technologies, as well as better. This guide gives the correlation between 49 of. 0 purpose to describe the conditions under which our employees my use their own devices at work. After considering more than a year’s. Web the world’s leading cybersecurity guidance is getting its first complete makeover since its. Ad haven't done a dfars assessment? It also gives advice on creating related security policies. Web the world’s leading cybersecurity guidance is getting its first complete makeover since its release nearly a decade ago. Web sans has developed a set of information security policy templates. This practice guide provides an example. Ad haven't done a dfars assessment? Web nist seeks feedback on whether this draft revision addresses organizations’ current and anticipated future. Web byod policy template 1. Web 62 effective cybersecurity solution for byod. This guide gives the correlation between 49 of. This publication provides recommendations for securing byod devices used for telework and remote access, as well as those directly attached to the. Web your own device (byod). The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal agencies. Web each telework device is controlled by the organization, a third party (such. The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal agencies. This practice guide provides an example. 0 purpose to describe the conditions under which our employees my use their own devices at work. After considering more than a year’s. Web this publication provides information on security considerations for several types of remote access solutions, and it makes recommendations for securing a variety. Web protected when it is accessed from personal devices poses unique challenges and threats. Web your own device (byod). Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). It also gives advice on creating related security policies. Security for enterprise telework, remote access, and bring your own device (byod) solutions; This guide gives the correlation between 49 of. Ad haven't done a dfars assessment? Finding an effective solution can be challenging due to the 63 unique risks that byod deployments impose. Cybersecurity challenges, is aligned with leading practices. Web 62 effective cybersecurity solution for byod. Web sans has developed a set of information security policy templates. Bring your own device (byod). the public comment period is open through may 3,. These are free to use and fully customizable to your company's it security practices. Web may 6, 2013 download all papers are copyrighted. Web nist seeks feedback on whether this draft revision addresses organizations’ current and anticipated future. It also gives advice on creating related security policies. 0 purpose to describe the conditions under which our employees my use their own devices at work. The protection of controlled unclassified information (cui) resident in nonfederal systems and organizations is of paramount importance to federal agencies. Web sans has developed a set of information security policy templates. This practice guide provides an example. These are free to use and fully customizable to your company's it security practices. Web 62 effective cybersecurity solution for byod. Security for enterprise telework, remote access, and bring your own device (byod) solutions; Cybersecurity challenges, is aligned with leading practices. The growing ubiquity of computing devices, whether it is a home computer or a personal smartphone, means that more and more staff are using their. To improve the security of organizations’ telework and remote access technologies, as well as better. Web itl march 2020 bulletin: Web may 6, 2013 download all papers are copyrighted. Web byod policy template 1. This guide gives the correlation between 49 of. Web this publication provides information on security considerations for several types of remote access solutions, and it makes recommendations for securing a variety.PDF Télécharger byod mobile security policy Gratuit PDF
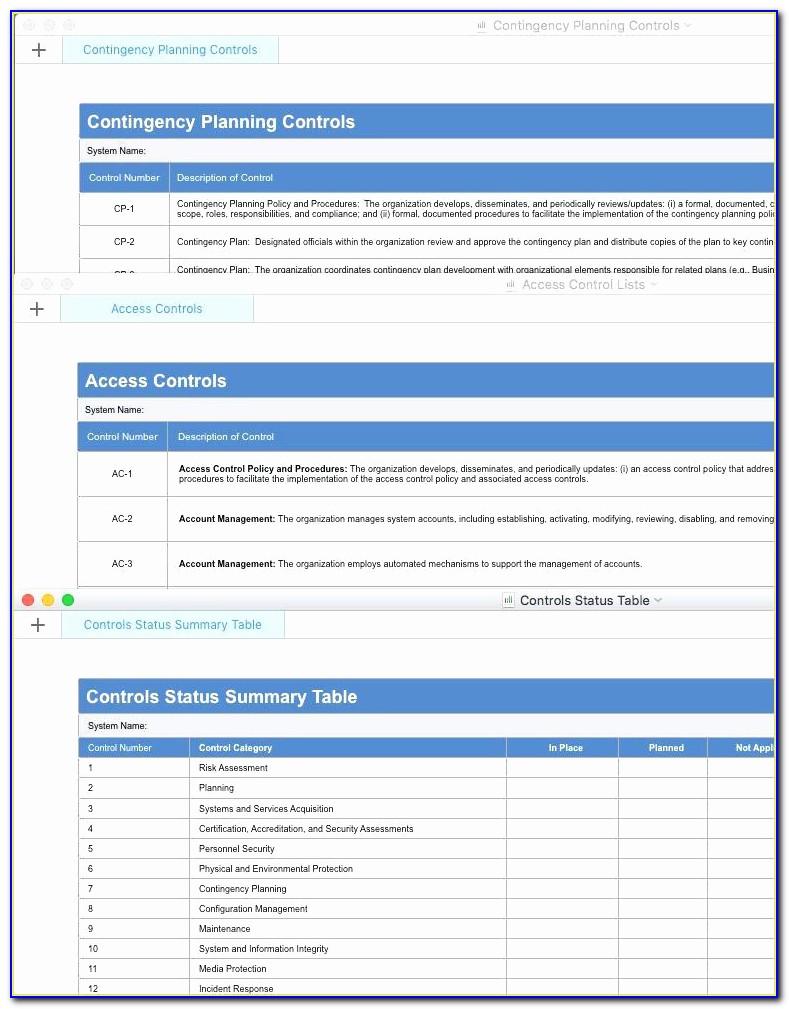
Nist 800171 Access Control Policy Template
BYOD Policy Template 1 Free Templates in PDF, Word, Excel Download
Download BYOD Policy Sample 1 for Free Page 5 FormTemplate
BYOD Policy Template
Free Byod Policy Template
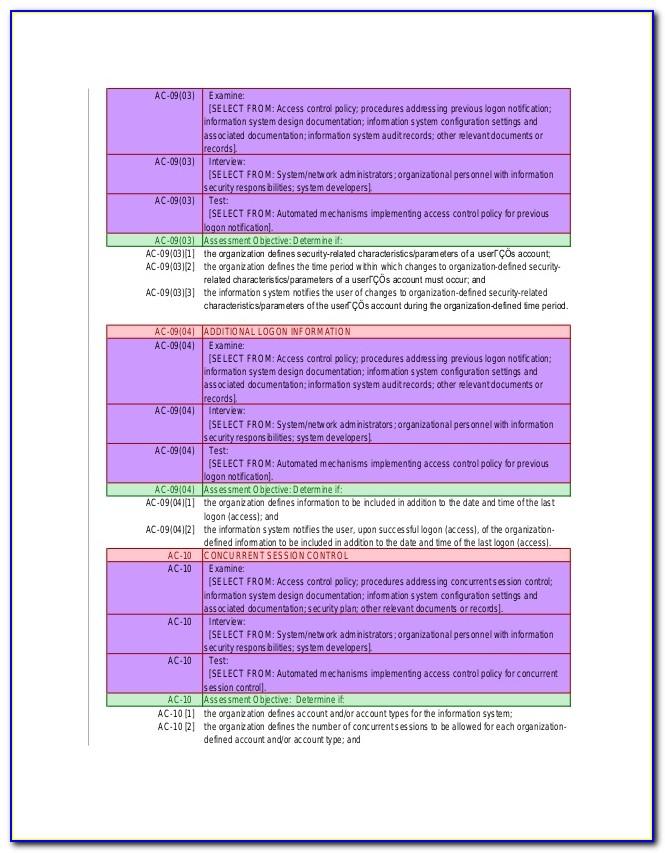
Nist Audit Policy Template
Free Byod Policy Template
Nist Access Control Policy Template
No Cell Phone Policy At Work Template
After Considering More Than A Year’s.
Finding An Effective Solution Can Be Challenging Due To The 63 Unique Risks That Byod Deployments Impose.
Web Nist Seeks Feedback On Whether This Draft Revision Addresses Organizations’ Current And Anticipated Future.
Web Protected When It Is Accessed From Personal Devices Poses Unique Challenges And Threats.
Related Post: