Aws Threat Model Template
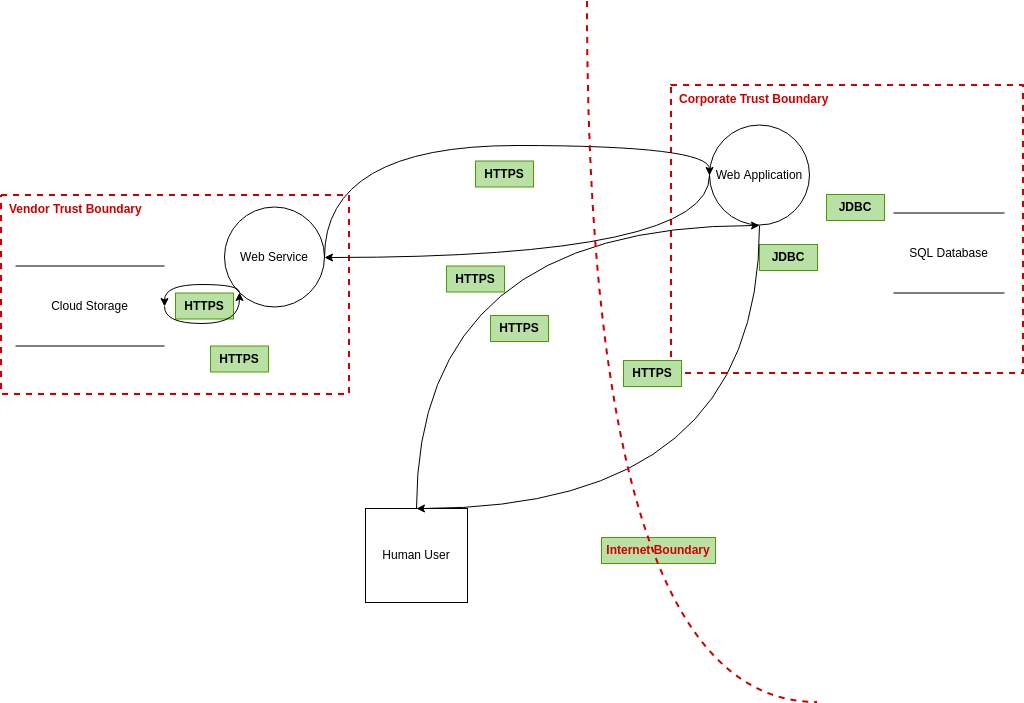
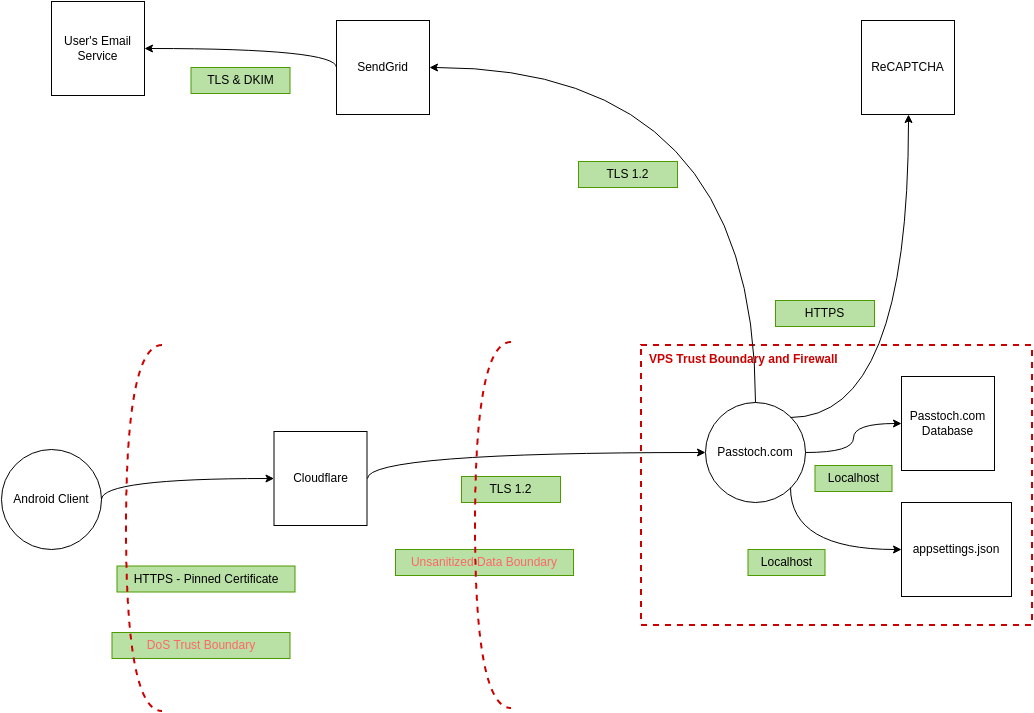
Aws Threat Model Template - Microsoft threat modeling tool template containing aws components and services. The aws templates include the. Discover how threatconnect can help you respond to threats before they harm your business. There are a number of strategies and. Web aws template for microsoft threat modeling tool. Web aws microsoft threat modeling tool template. Web this section describes how to populate the provided threat model template (and this threat model template can be used without threatware, but threatware makes it simple to verify. Web aws and its partners offer a wide range of tools and features to help you to meet your security objectives. Web to make threat modeling highly replicable, we are able to create a model from a template. You do not need to be a security expert. Discover how threatconnect can help you respond to threats before they harm your business. However, threat modeling is one. Web this section describes how to populate the provided threat model template (and this threat model template can be used without threatware, but threatware makes it simple to verify. Ad threat intelligence platform for cybersecurity, cloud security & more. Ad parse,. Discover how threatconnect can help you respond to threats before they harm your business. Microsoft threat modeling tool template containing aws components and services. However, as new cloud capabilities and services. Web threat model generation process using the iriusrisk api. In my experience, all threat modeling approaches are similar; Open a threat model from which you would like to create a template. The cloud is an enabler for transformations in business and information technology. These tools mirror the familiar controls you deploy within your on. At a high level, they follow these broad steps: Microsoft threat modeling tool template containing aws components and services. There are a number of strategies and. These tools mirror the familiar controls you deploy within your on. Web aws iq websites & mobile applications databases & analytics networking & security machine learning productivity & collaboration cost optimization other. However, threat modeling is one. Identify assets, actors, entry points, components, use cases, and trust levels, and include these in a. However, threat modeling is one. Navigate to the icon on the diagram screen. Web aws iq websites & mobile applications databases & analytics networking & security machine learning productivity & collaboration cost optimization other. Ad parse, normalize, and analyze tb/day of data, 12+ months retention in security data lake. Web this cheat sheet aims to provide guidance on how to. Select save threat model as template. Web aws iq websites & mobile applications databases & analytics networking & security machine learning productivity & collaboration cost optimization other. In my experience, all threat modeling approaches are similar; Generic threat modeling elements are: Threat modeling serves to identify threats and preventive measures for a system or application. Open a threat model from which you would like to create a template. Threat modeling is about identifying potential threats for your organization and in particular for each of your cloud workloads. Web aws microsoft threat modeling tool template. The created docker templates are based on owasp container. Ad launch your project on the most comprehensive & broadly adopted cloud. Select save threat model as template. Threat modeling is about identifying potential threats for your organization and in particular for each of your cloud workloads. Web aws template for microsoft threat modeling tool. The aws templates include the. Open a threat model from which you would like to create a template. In my experience, all threat modeling approaches are similar; Web in this workshop, you will be introduced to some of the background and reasoning behind threat modeling and some of the tools and techniques for modeling systems, identifying. Select save threat model as template. Web threat model generation process using the iriusrisk api. Discover how threatconnect can help you respond. Web to make threat modeling highly replicable, we are able to create a model from a template. Web after creating some templates for aws it’s time to make a first step into containerization. Threat modeling serves to identify threats and preventive measures for a system or application. Discover how threatconnect can help you respond to threats before they harm your. Web building your cloud operating model. Ad launch your project on the most comprehensive & broadly adopted cloud platform. Web to make threat modeling highly replicable, we are able to create a model from a template. There are a number of strategies and. Web this guide presents an overview of the fundamentals of responding to security incidents within a customer’s amazon web services (aws) cloud environment. Identify a list of threats. Web aws iq websites & mobile applications databases & analytics networking & security machine learning productivity & collaboration cost optimization other. Threat modeling serves to identify threats and preventive measures for a system or application. Per threat, identify mitigations, which may include. Web this cheat sheet aims to provide guidance on how to create threat models for both existing systems or applications as well as new systems. These tools mirror the familiar controls you deploy within your on. Discover how threatconnect can help you respond to threats before they harm your business. Navigate to the icon on the diagram screen. In my experience, all threat modeling approaches are similar; However, threat modeling is one. Web aws and its partners offer a wide range of tools and features to help you to meet your security objectives. Open a threat model from which you would like to create a template. Web this section describes how to populate the provided threat model template (and this threat model template can be used without threatware, but threatware makes it simple to verify. These are some first steps to create templates for cloud based threat models. You do not need to be a security expert. Web aws and its partners offer a wide range of tools and features to help you to meet your security objectives. Discover how threatconnect can help you respond to threats before they harm your business. Ad threat intelligence platform for cybersecurity, cloud security & more. Per threat, identify mitigations, which may include. You do not need to be a security expert. Web to make threat modeling highly replicable, we are able to create a model from a template. By developing threat models, organizations can identify threats and mitigations before an unauthorized user can. These tools mirror the familiar controls you deploy within your on. Select save threat model as template. The cloud is an enabler for transformations in business and information technology. Web in this white paper, discover how to build a secure, accurate and consistent threat modeling process for the cloud, including: Web this section describes how to populate the provided threat model template (and this threat model template can be used without threatware, but threatware makes it simple to verify. Web this cheat sheet aims to provide guidance on how to create threat models for both existing systems or applications as well as new systems. In my experience, all threat modeling approaches are similar; At a high level, they follow these broad steps: Data enrichment to reduce false positives & add context to alerts | powerful automationawsthreatmodelingtooltemplate/AWSThreatModelingExample.tm7 at
Sdl threat modeling tool netapps passsr
Aws Threat Modeling Tool Template
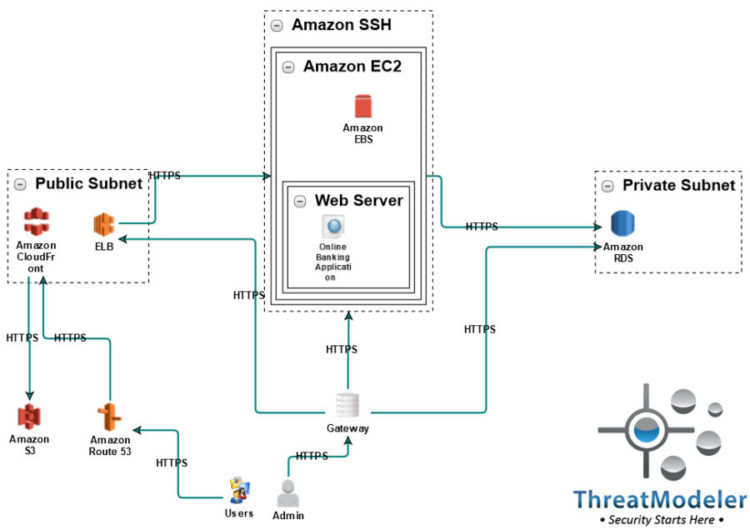
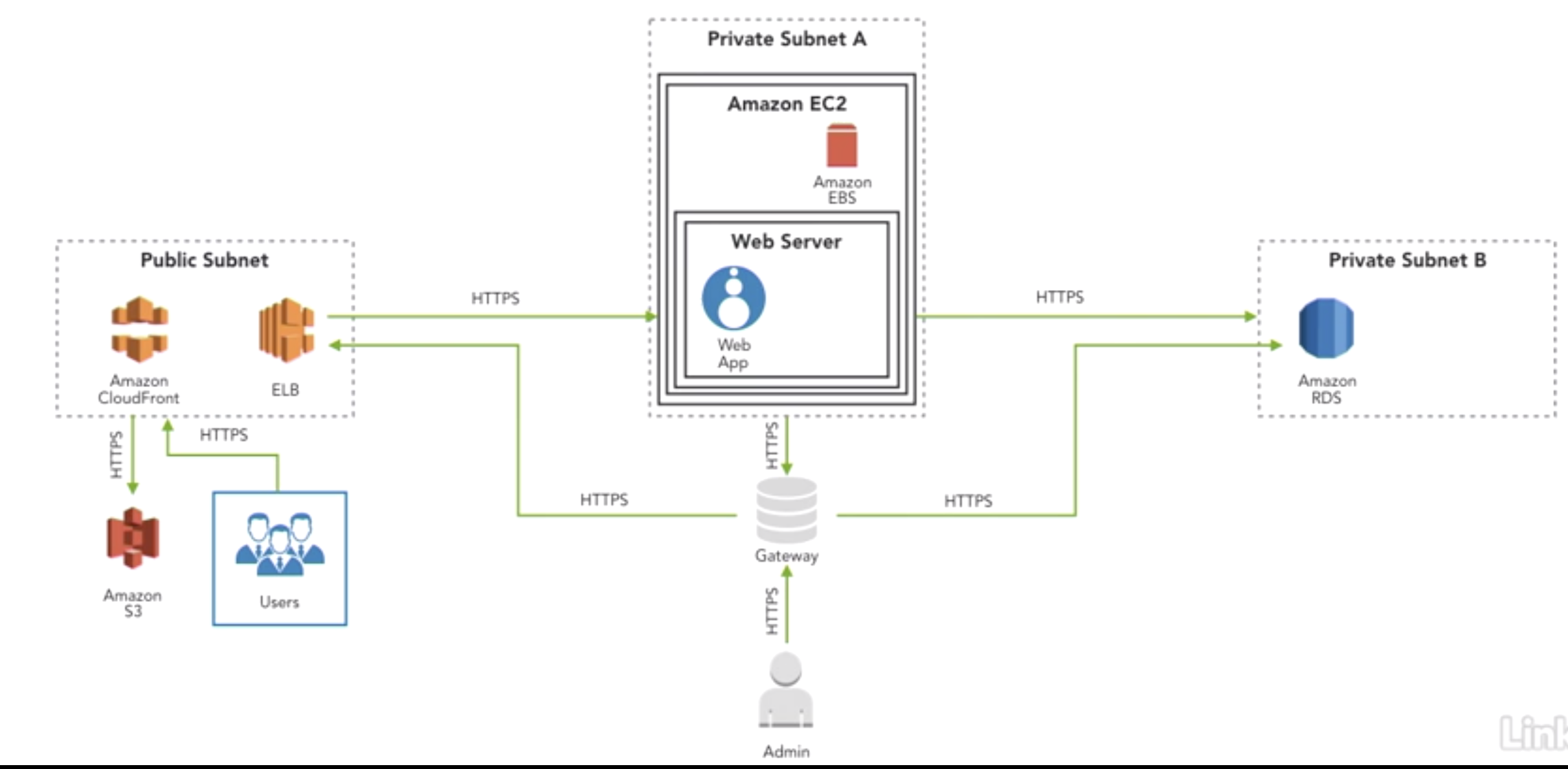
AWS Cloud Threat Modeling Reduces Risk ThreatModeler
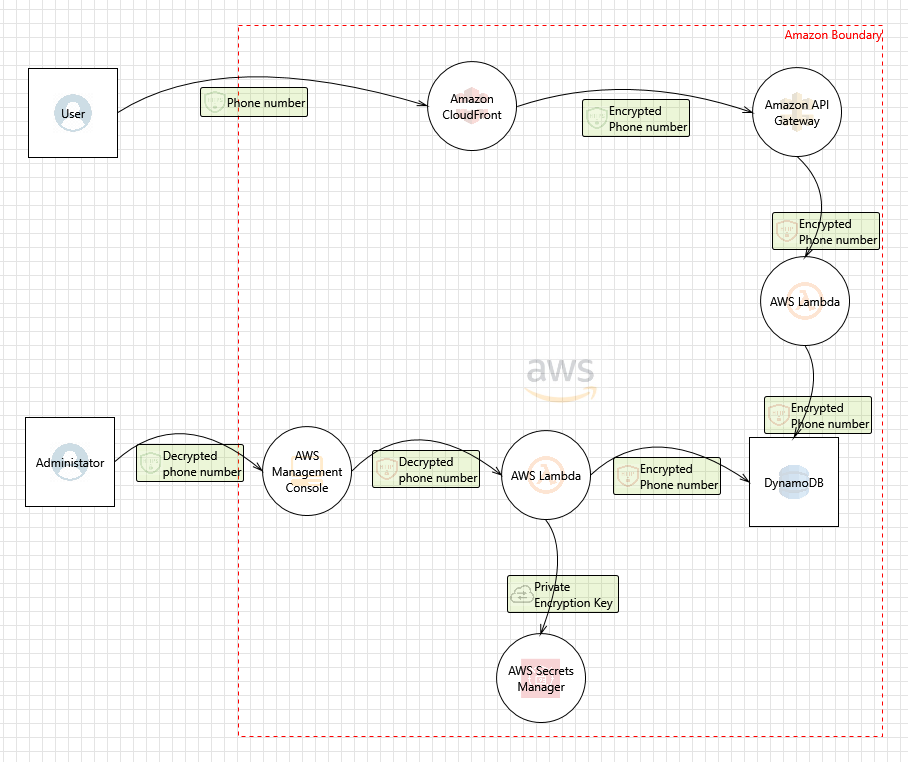
AWS Solutions Architect Associate2 Data Security
Creating Your Own Personal Threat Model
STRIDE Threat Model 威胁模型图 Template
Alternatives and detailed information of threatmodeltemplates
Threat Modeling AWS Announcing ThreatModeler Cloud Edition
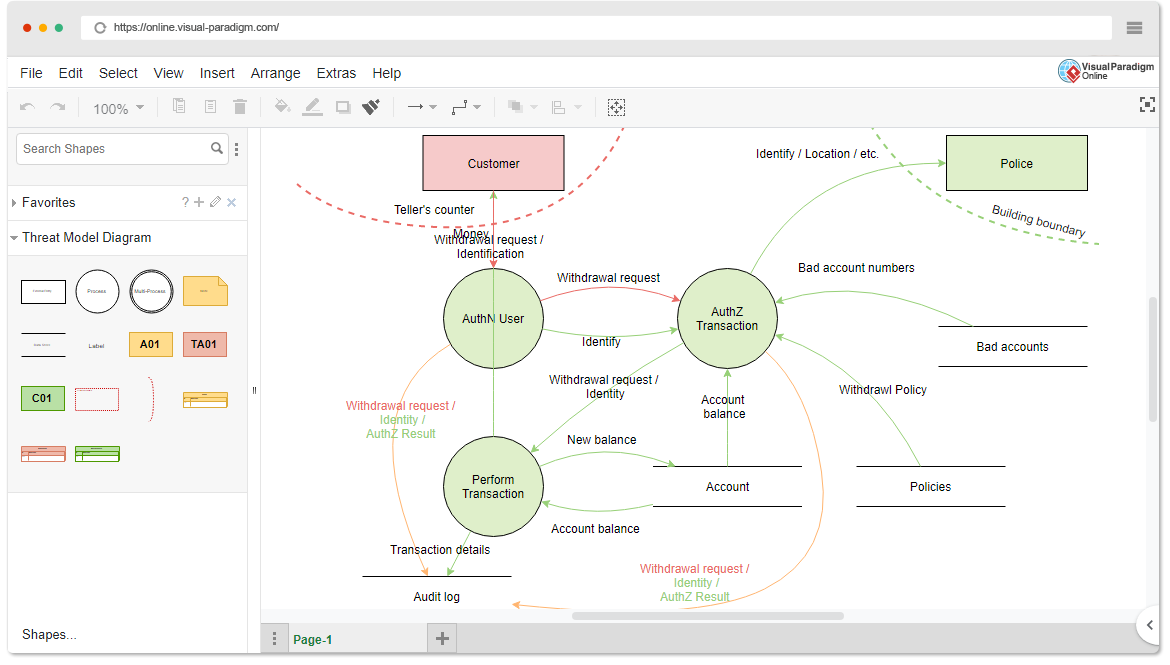
Sample Threat Model Threat Model Diagram Template
Navigate To The Icon On The Diagram Screen.
Web Building Your Cloud Operating Model.
However, As New Cloud Capabilities And Services.
Web After Creating Some Templates For Aws It’s Time To Make A First Step Into Containerization.
Related Post: